Loading...


Part 1

Presented By
Nischith B.M.


Agenda
- Security Principles
- Authentication vs Authorization
- Understanding WEP
- WEP - Authentication Phase
- Stream Cipher
- IV - Initialization Vector
- WEP Keys
- RC4 Encryption Algorithm
- Why WEP is a Failure !!!
- Say Hello to WPA

Security Principles
- What is security ?
- Good Security Thinking
- Don't talk to anyone you don't know
- Accept nothing without a guarantee
- Treat everyone as an enemy until proved otherwise
- Don't trust your friends for long
- Watch the ground you are standing on for cracks

Authentication vs Authorization
- Distinguish the "good guys" from the "bad guys".
- Decide to "let him in or not"

Understanding WEP
- What is WEP ?
- Reasonably strong. Really !!!
- Self-synchronizing
- Use of 40-bit keys
- Authentication Phase
- Encryption Phase

WEP - Authentication Phase
- No secret token is exchanged upon authentication
- Need of identifying every packet
- WEP-based authentication


Stream Cipher
String:
Key:

IV - Initialization Vector
- IV is transmitted openly with the encrypted frame
- Same IV value should never be used twice with a given secret
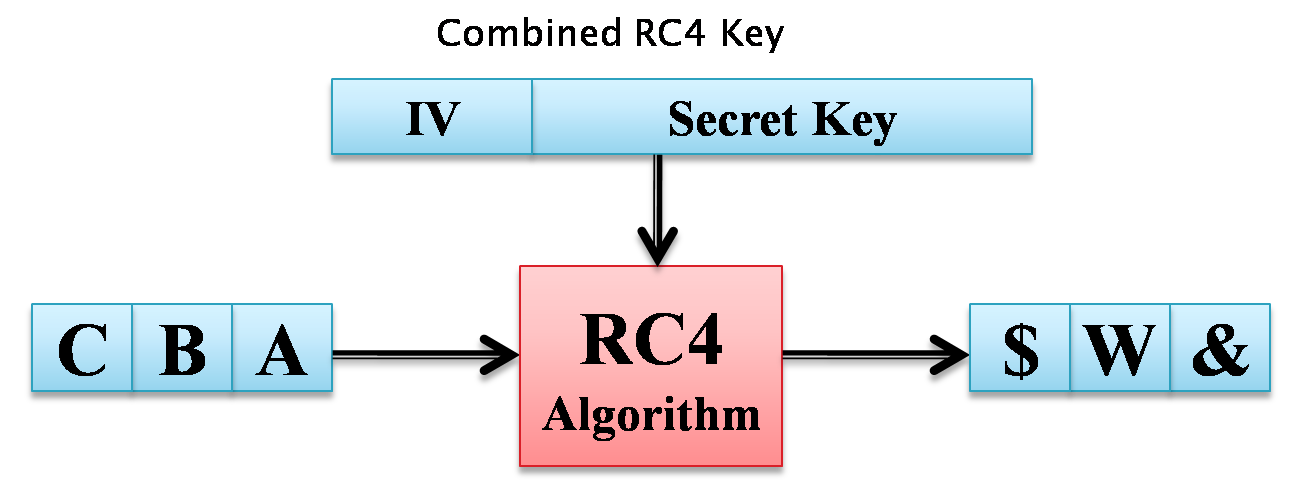
- A 24-bit number - about 17 million IV values possible
- Other causes of IV reuse

WEP Keys
- Fixed length - 40 bits or 104 bits
- Static
- Shared
- Symmetric
- Two types of WEP keys
- Default key(s)
- Key mapping key(s)

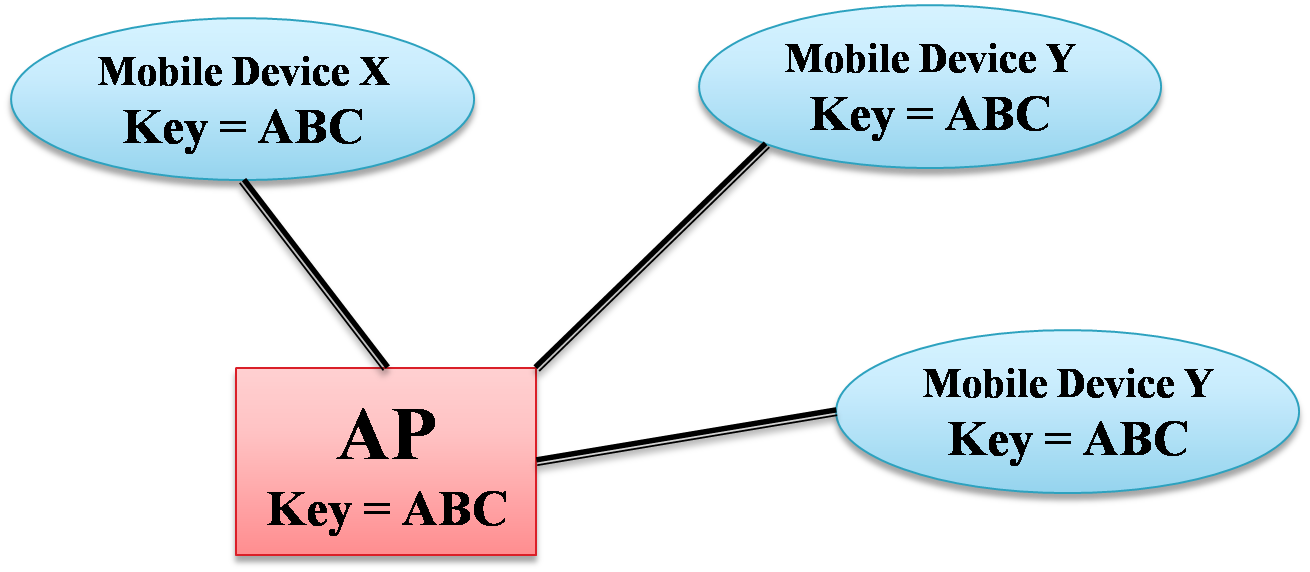
Default Keys
- All devices use the same key
- Medium size installations

Key Mapping Keys
- Each device will have its own key
- Large installations
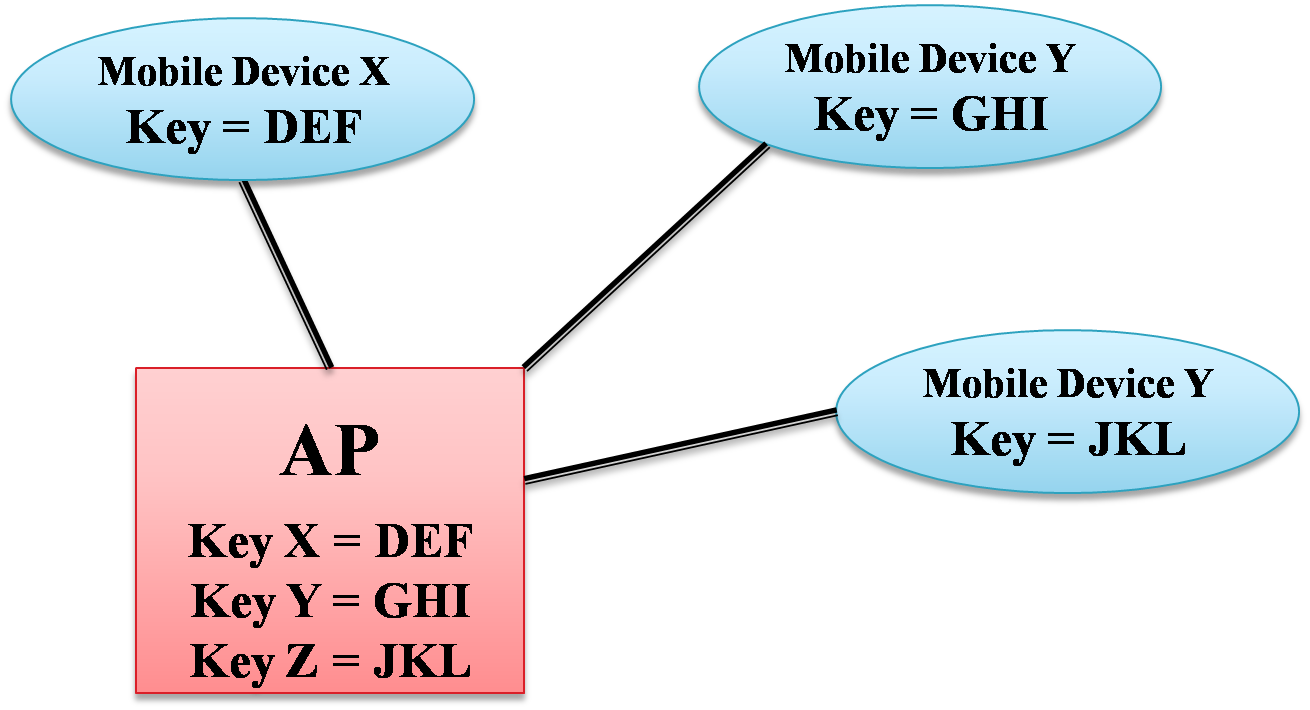
- How does the AP send a broadcast message?

ICV - Integrity Check Value
- CRC - detects accidental errors
- ICV is similar to the CRC
- ICV is computed and added on before encryption
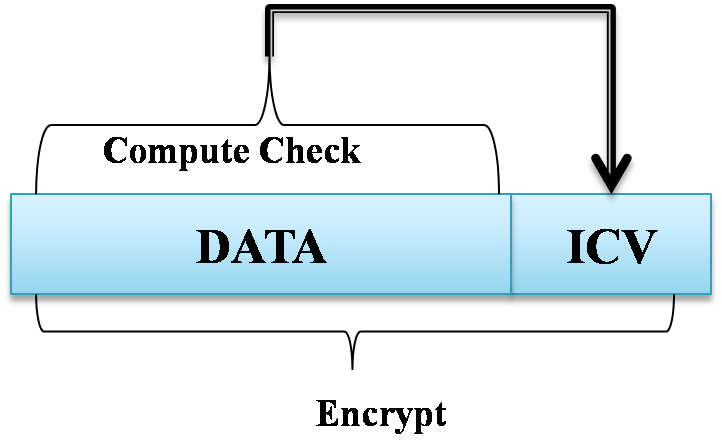

Preparing the Frame
- Append IV to secret WEP key
- Initialize the RC4 encryption engine


RC4 Encryption Algorithm
- Used for both encryption and decryption
- Easy to implement
- Uses Exclusive OR (XOR) operation
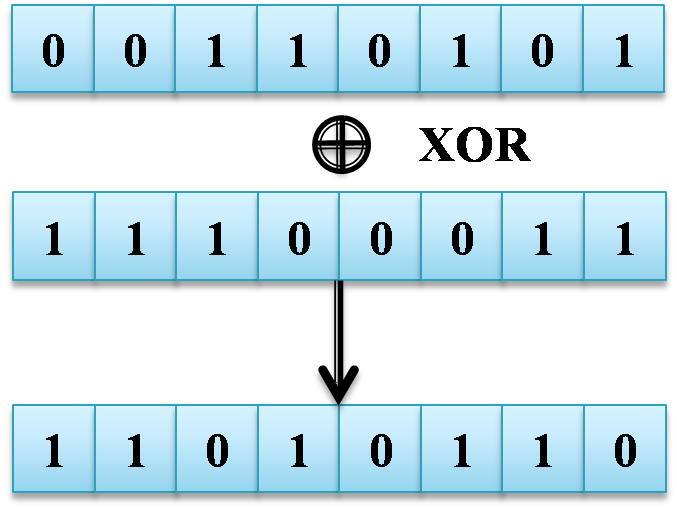
-
Encryption: Plaintext
 Random = Ciphertext
Random = Ciphertext
Decryption: Ciphertext Random = Plaintext
Random = Plaintext

Why WEP is Not Secure ?
- Authentication
-
If Plaintext
 Random = Ciphertext
Random = Ciphertext
Then Ciphertext Random = Plaintext
Random = Plaintext
-
If Plaintext
 Random = Ciphertext
Random = Ciphertext
Then Ciphertext Plaintext = Random
Plaintext = Random
Game is Over.. !!!
-
If Plaintext
- Reply prevention
- It simply doesn't exist

Say Hello to WPA
- IEEE 802.11i, RSN and TKIP
- What is WPA ?
- WPA vs RSN
- Security Context
- Keys

Abbreviations Used
| WEP | Wired Equivalent Privacy |
|---|---|
| RSN | Robust Security Network |
| TSN | Transitional Security Network |
| WPA | Wi-Fi Protected Access |
| AES | Advanced Encryption Standard |
| TKIP | Temporal Key Integrity protocol |
| IV | Initialization Vector |
| ICV | Integrity Check Value |
| CRC | Cyclic Redundency Check |
THANK YOU